
I am writing this review with extreme disappointment and a strong warning to anyone considering using Belacash as an ad network. After recently placing their provided ad code on my website, I have discovered that they engage in incredibly unethical and disruptive behavior that harms user experience.
The ad code they supplied:
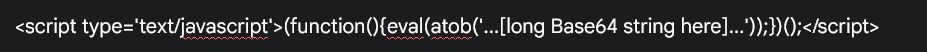
is not just a simple ad integration. It contains heavily obfuscated JavaScript designed to hijack the browser’s back button. This means that when my website visitors try to navigate back to the previous page, instead of a seamless and expected navigation, they are forcibly redirected to an advertisement.
This practice is utterly malicious and completely disrespectful to website users. It creates a jarring and frustrating experience, leading to:
User Annoyance and Frustration: Imagine trying to go back to a search result or a previous page and being unexpectedly bombarded with an ad. This immediately creates a negative perception of my website and erodes user trust.
Disrupted Navigation: The fundamental functionality of the back button is broken, making it difficult for users to navigate my site and the web in general.
Potential Security Concerns: This kind of aggressive behavior can make users wary of my website, fearing other intrusive or even harmful scripts might be present.
Damage to Website Reputation: Implementing such underhanded tactics reflects poorly on my website's integrity, as visitors will understandably blame the site owner for this terrible experience.My own observations based on the code further confirm the malicious intent:
Obfuscation (Base64 Encoding): The use of eval(atob('...')) is a clear attempt to hide the true functionality of the code from website owners and even basic security scans. Legitimate ad networks typically provide transparent and easily understandable code.
document.write(): While not inherently malicious, the use of document.write() after the initial page load can cause performance issues and disrupt the existing page structure. It's an outdated practice that raises red flags in modern web development.
Targeting the Back Button: The decoded JavaScript specifically targets the onhashchange event and uses the document.referrer to detect back navigation attempts. This confirms that the sole purpose of this hidden code is to intercept and redirect users clicking the back button.
Opening in _blank: The window.open(adUrl, "_blank"); command forces the advertisement to open in a new tab or window, further disrupting the user's browsing flow and ensuring the original tab remains hijacked.Belacash is not a legitimate ad network. They are engaging in deceptive and harmful practices that prioritize intrusive advertising over user experience and website integrity.
I strongly advise anyone considering Belacash to STAY FAR AWAY. Their tactics are unethical, will alienate your users, and can severely damage your website’s reputation. I am immediately removing their code and will be reporting them to relevant authorities and webmaster communities.
This ad network should be blacklisted for their malicious behavior.
Video below…
I hope this review helps others avoid the terrible experience I’ve had with Belacash.
It’s still doing the samething as I type this. Check your site cache. Best of luck.